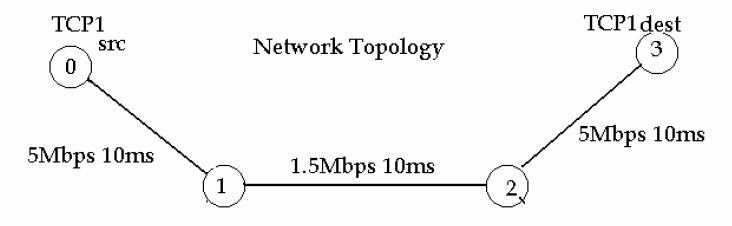
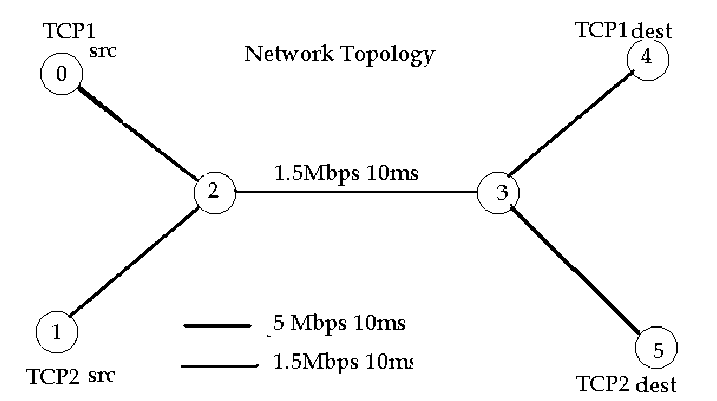
|
T. Andrew Yang
|
Last updated: 03/05 |
||||
1.A (10 pts) 1.D (15 pts) Problem 3.10 (S: p.84) Assignment 2: new due date - 3/31 Cisco IOS commands and NS-2:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios122/122mindx/l22index.htm
(If this link does not work, try an older version at http://www.cisco.com/univercd/cc/td/doc/product/software/ios120/120mindx/l20index.htm
or http://www.cisco.com/univercd/cc/td/doc/product/software/ios111/supdocs/sbook/).
2.A (30 pts, 15 pts per script) Draw a network diagram for each of the following scripts. For example diagram, see the Malik's book (e.g., Figure 3-2 on p.40). Explain what each of the scripts would accomplish.
hostname Switch-B vtp mode transparent vlan 10 name Engineering
vlan 20 name Sales vlan 30 name interface range fastEthernet0/1 – 16 switchport mode access switchport access vlan 10 interface range fastEthernet0/17 – 32 switchport mode access switchport access vlan 20 interface range fastEthernet0/33 – 48 switchport mode access switchport access vlan 30 interface vlan 10 ip address 192.168.10.1 255.255.255.0
Assignment 3 Go to the Index Projects
The focus of this project is to
explore features of the ns-2 network simulator, by creating and
running sample ns applications. To successfully complete the project,
each team should check out the following ns-2 resources as well as the
ns-2 user manual.
(Acknowledgement: The project was modified from sample projects by Dr. Papadopoulos, USC.)
Go to the Index
As you have experienced in the
first project, NS-2 provides rich features for users to simulate
network configurations and protocols. It is a useful and widely used
simulation and devleopment environment for conducting simulation-based
network
research, from local area networks (LANs) to mobile ad hoc networks
(MANETs).
An example research project using NS-2 is the "Scenario-based Performance Evaluation of Secure Routing in MANETs", by Sadasivam, Changrani, and Yang. A worling paper reporting the current findings of that project is available here (MANETII05-draft.pdf). The purpose of this project is two-fold:
I. Part A: Project Design (Due: 4/7)
Note: Every member of each team
should be prepared to answer questions during your team's 'project
design' presentation.
http://en.wikipedia.org/wiki/RFID
http://www.wireless.ucla.edu/rfid/winrfid/ http://www.rfidjournal.com/ Questions to answer: Is NS-2 ready to simulate an RFID wireless network? If yes, what are the needed tools, resources, and procedure? If not, how could NS-2 be extended to support such projects?
Questions to answer: Are the proposed performance metrics appropriate? Are there any additional metrics that should be added? What additional resources are needed to implement the proposed project? What is the procedure of implementation?
Questions
to answer: How would a GUI designer be added to the NS-2? What
capabilities should such a designer have? What network devices
(routers, switches, hosts, servers, ...) should be included in such a
virtual network designer? If more advanced devices (such as firewalls,
VPN servers, etc.) are to be added, what challenges would you need to
face?
Using NS-2 to evaluate the
security of an RFID wireless network?
Extending NS-2 to become a virtual network designer for VPN network? Extending NS-2 to support encryption/decryption? Can NS-2 be used to build a virtual network for experimenting attacks at the network? ... What to hand in for Part A
II. Part B: Final Report (Due: 4/28)
What to hand in for Part B
a. A final report that contains
all three parts listed above (detailed survey, detailed design,
up-to-date references),
b. An oral presentation of the report to the class on the due date. It is highly recommended that Powerpoint slides be used for the presentation. Go to the Index
|
|